
They might run occasionally or on a scheduled basis some scans that might find vulnerabilities in your application. But, how do we minimize that possibility? It's not rocket science that you should first have a security-oriented mindset in your team, but also include some SCA (Source Composition Analysis), SAST (Static Application Security Testing), and DAST (Dynamic Application Security Testing) in your CI CD setup.
For some time, GitHub has been offering Github Advanced Security to help you improve and maintain the quality of your code, such as code scanning, secret scanning, and dependency review. How about teams and enterprises that are Microsoft-oriented but using Azure DevOps for project management, code storage, CI-CD, and testing? Well, for a long time, Azure DevOps was missing this kind of feature, so the alternative was to use solutions from other vendors through Azure DevOps Marketplace extensions or CLI runs.
Finally, in September 2023, Microsoft introduced GitHub Advanced Security for Azure DevOps as a globally available tool, directly integrated into Azure DevOps. For you, who have used GitHub Advanced Security, it will be quite familiar, since they are just replicating the same functionalities from Github to Azure DevOps. So let's start with the basics of the tool.
GitHub Advanced Security for Azure DevOps includes:
• Secret Scanning push protection: check if code pushes include commits that expose secrets such as credentials
• Secret Scanning repo scanning: scan your repository and look for exposed secrets that were committed accidentally
• Dependency Scanning – search for known vulnerabilities in open-source dependencies (direct and transitive)
• Code Scanning – use CodeQL static analysis engine to identify code-level application vulnerabilities such as SQL injection and authentication bypass
To this day, most of the commonly used languages are supported: C/C++, C#, Go, Java, JavaScript/TypeScript, Kotlin, Python, Ruby, and Swift.
How to enable GitHub Advanced Security
Advanced Security can be enabled on 3 different levels in Azure DevOps:
• Repository level
• Project level
• Organization level
Each of these are easy to kick off but the impact might be larger on project and organization level. You want to make sure that permission setup for your repositories is configured in a way so that you do not expose any of the vulnerabilities to users who should not have access to these. Due to this factor, we will start today with Repository level onboarding.
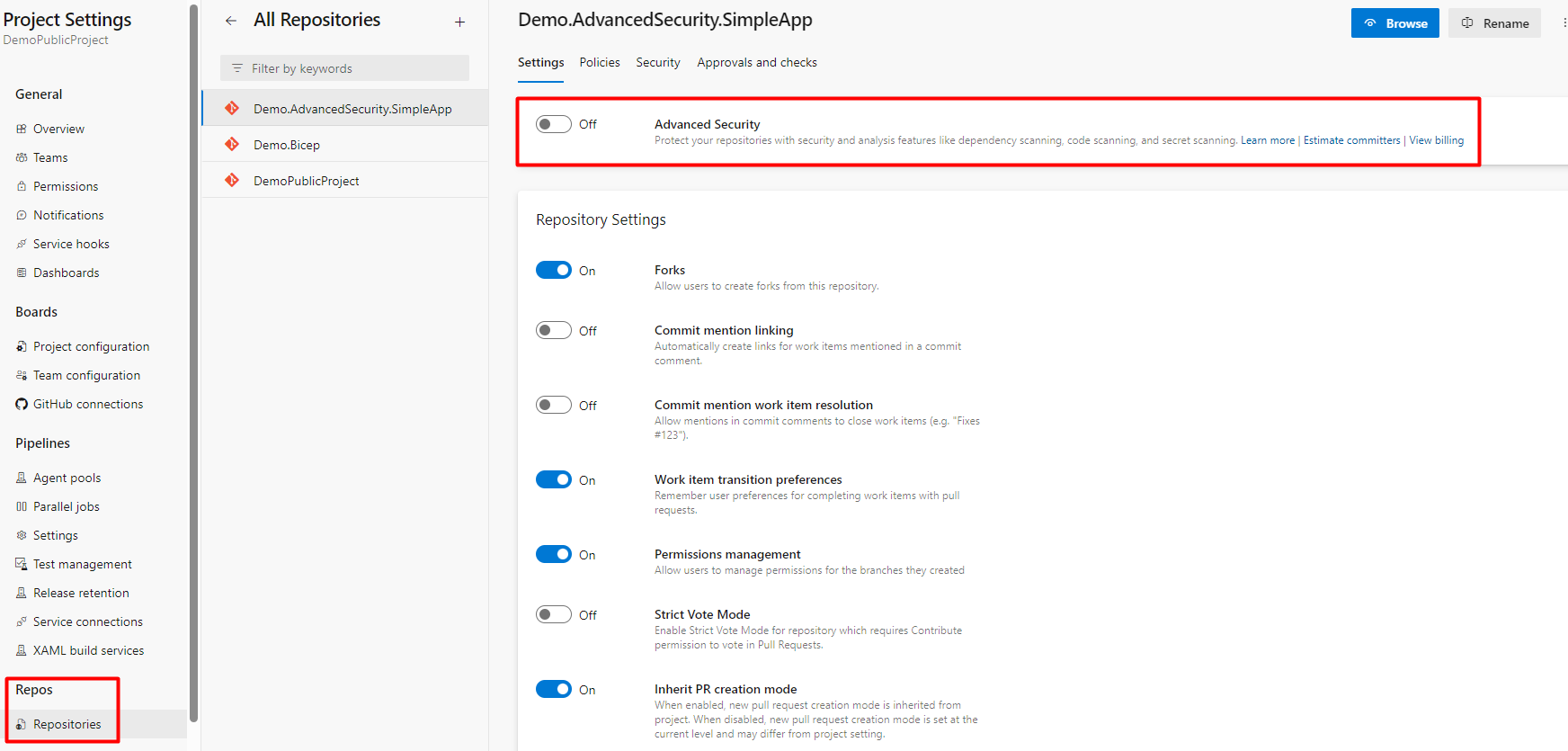
1. Go to Project Settings
2. Under Repos, go to Repositories
3. Find a Repository where you want to enable Advanced Security
4. Toggle the button, and TURN ON Advanced Security
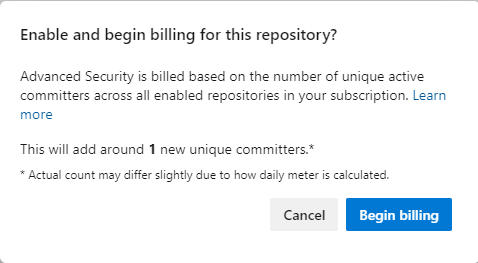
5. Pop up window will show you an estimate of unique committers that will be billed additionally to your Azure Subscription that is connected to the Azure DevOps organization
6. Begin billing
Now you have enabled the Advanced Security for the repository. With this action, now by default, Secret Scanning is taking place for this repository and all secrets that you try to push to the repository, such as Service Principal Client Secret, Storage Account Keys, DB Connections, etc, will be prevented and your commit will be rejected with the explanation. Also, existing secrets that are in your repository will be reported under the Advanced Security -> Secrets tab. More on this topic will be described below.
CI CD
After introducing the Advanced Security, only Secret scanning is in place by default. In order to get all the benefits of the toolset, such as dependency scan and code scan, you need to add some steps in your CI CD pipeline so that the scan is performed.
1. Open Pipelines -> New pipeline (if there is no existing)
2. Azure Repos Git YAML
3. Find your repository and select the starter pipeline
4. Add your regular build steps
a. In this case, we have a simple javascript application with a simple build process
b. The build process will vary based on programming language(s) and technology(s)
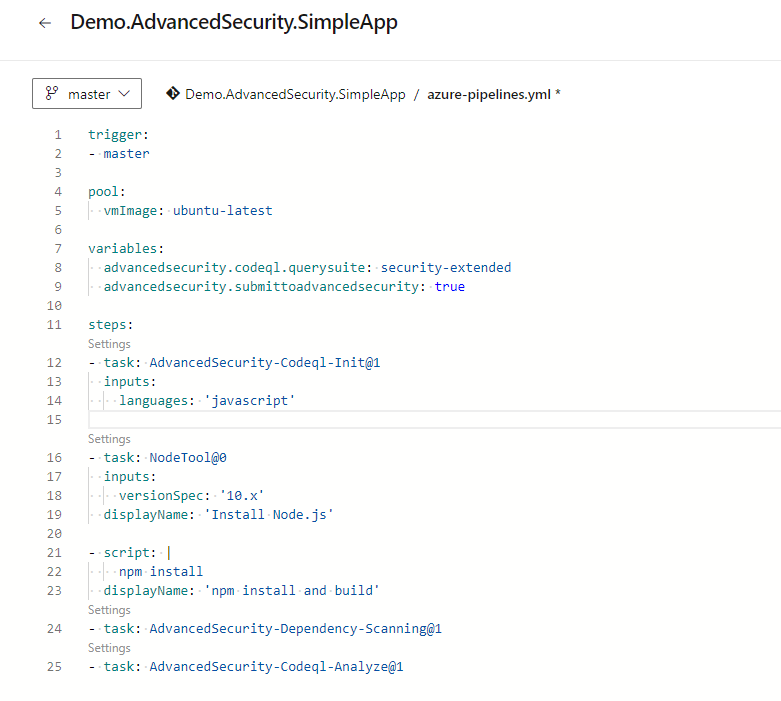
5. Add Advanced Security Steps
a. AdvancedSecurity-Codeql-Init@1
i. Setting up language and query suite
ii. Suites available: security-extended, code-scanning, security-experimental, security-and-quality. The suggestion is to start with security-extended which is the default.
b. AdvancedSecurity-Dependency-Scanning@1
i. Dependency scan execution and publishing results
c. AdvancedSecurity-Codeql-Analyze@1
i. Code Scan execution and publishing results
These 3 steps are minimal for running both Dependency and Code Scanning.
There are two more optional tasks:
- AdvancedSecurity-Codeql-Autobuild@1
o Attempts to build the repository by finding and building project files in the source folder
- AdvancedSecurity-Publish@1
o Enhances the data in the SARIF results file and publishes the results to the Advanced Security service. Even without this setup, the results will be automatically updated to the Advanced Security service under Repos.
Also, you can use variables to set specific details such as codec suite, submit to advanced security, etc. Click to Run the pipeline and wait for a successful outcome.
Results
Dependency Scanning
After the run in pipelines, the logs will show that the Advanced Security inventory is updated. Now you can view all dependencies in list view with the possibility to filter-branch, state, pipeline, package, and severity. You can see which alert is triggered, its severity, the vulnerable package, and when it was first detected.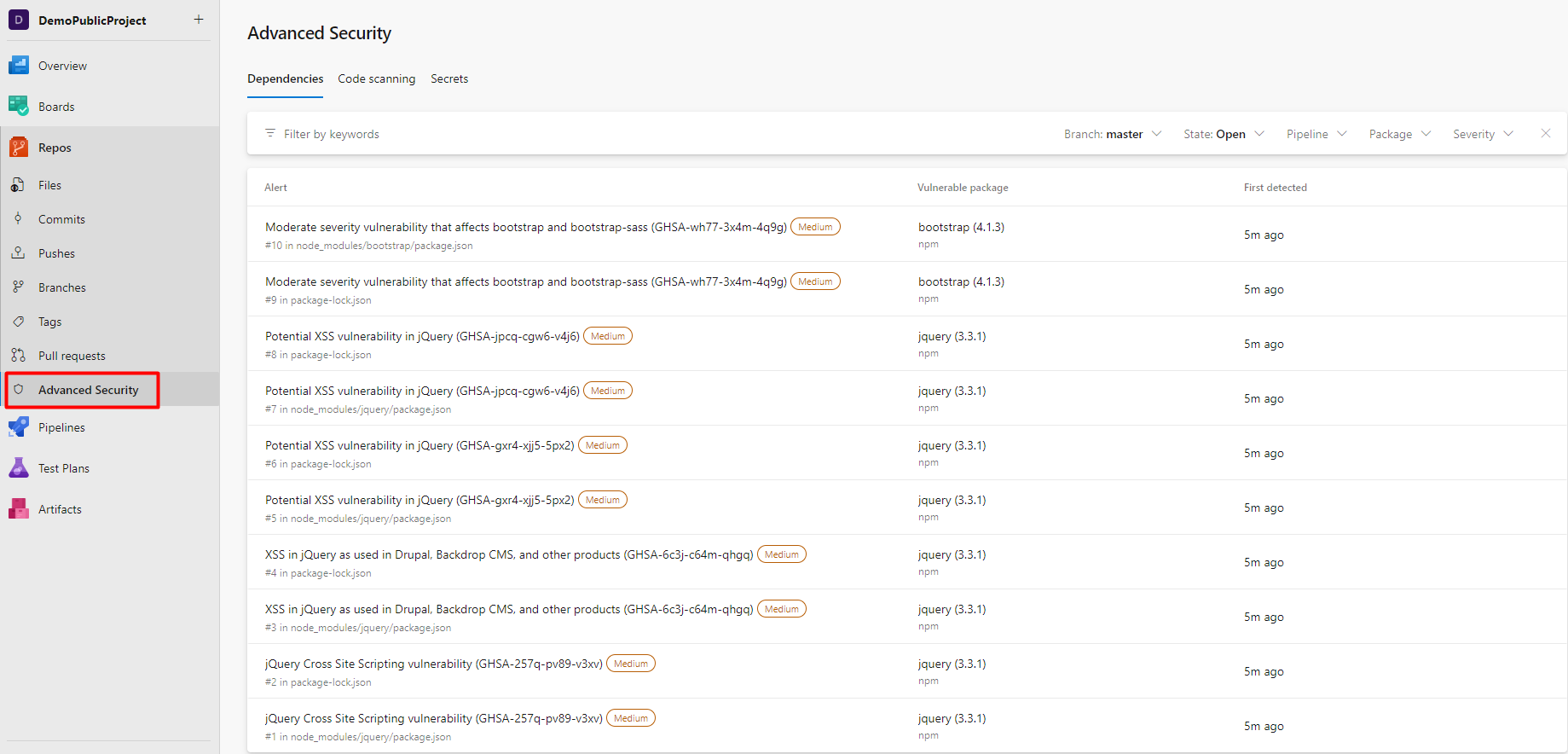
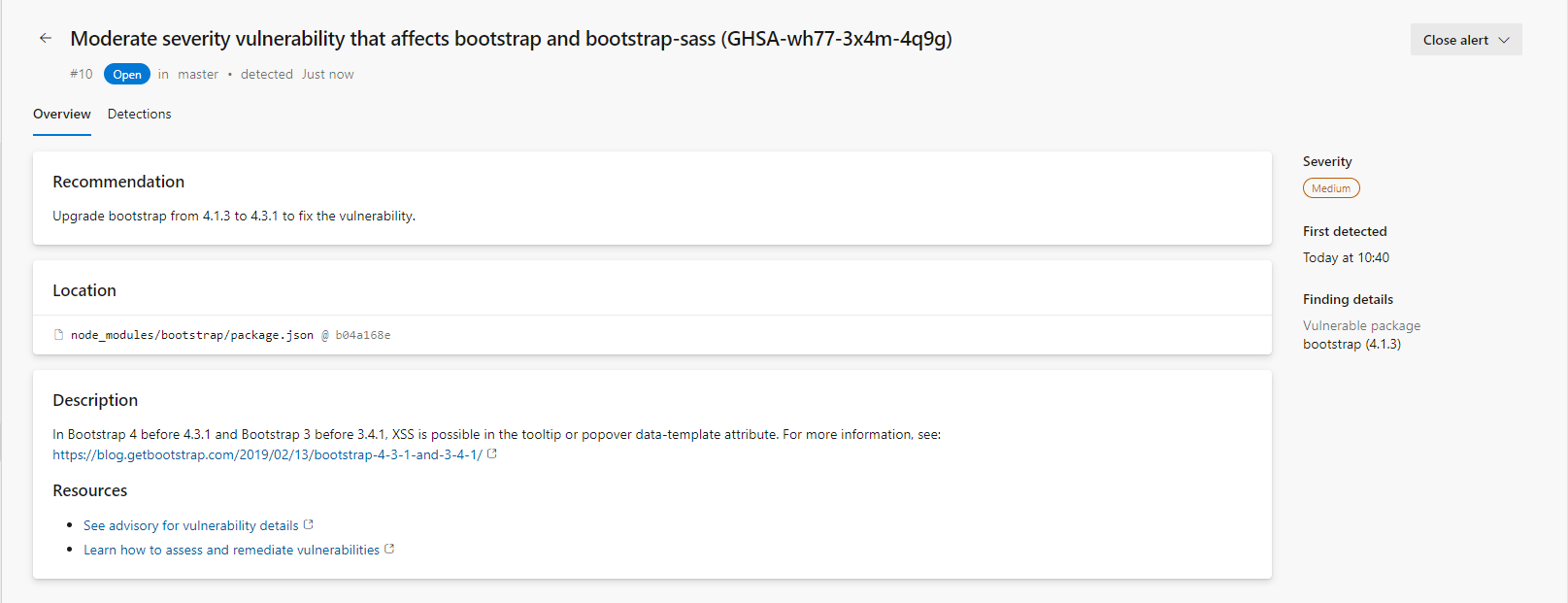
If you open one of the vulnerabilities, more details about it are shown, such as Recommendations, Location, Description, and Resources. You can also view all detections (pipelines) of this vulnerability in the current repo.
In order to fix the vulnerability, you should investigate and evaluate the recommended version to update the package. In our case, it is the bootstrap 4.1.3 version that is vulnerable and should be updated to version 4.3.1 to mitigate it.
The alert will automatically close if you fix the vulnerability and rerun the pipeline. If for some reason, you accept the risk or the alert is false positive, you can manually close the alert.
Code Scanning
The same approach is with code scanning. Inventory under Advanced Security -> Code scanning shows all vulnerabilities in the current repository, filtered by branch, state, pipeline, rule, and severity. You can view what alert is triggered, where it is found, severity, and when it is first detected.
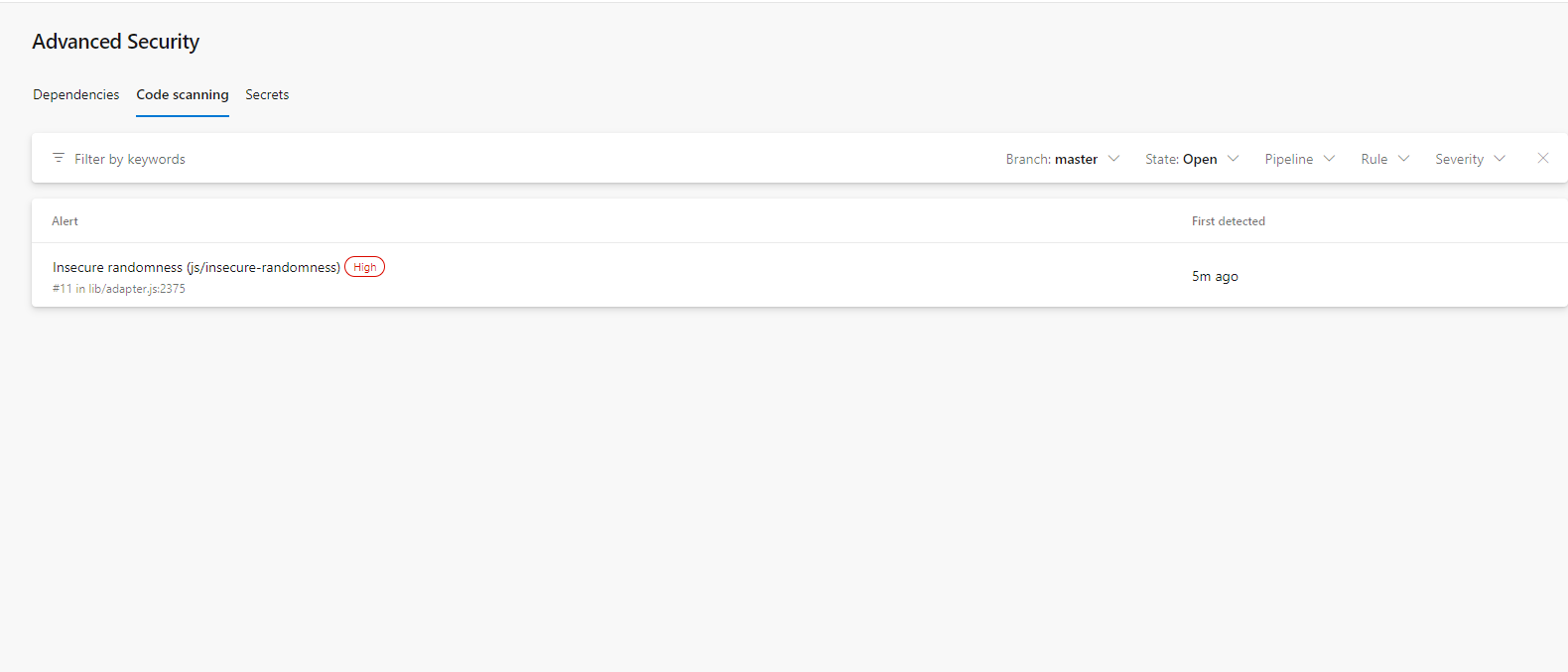
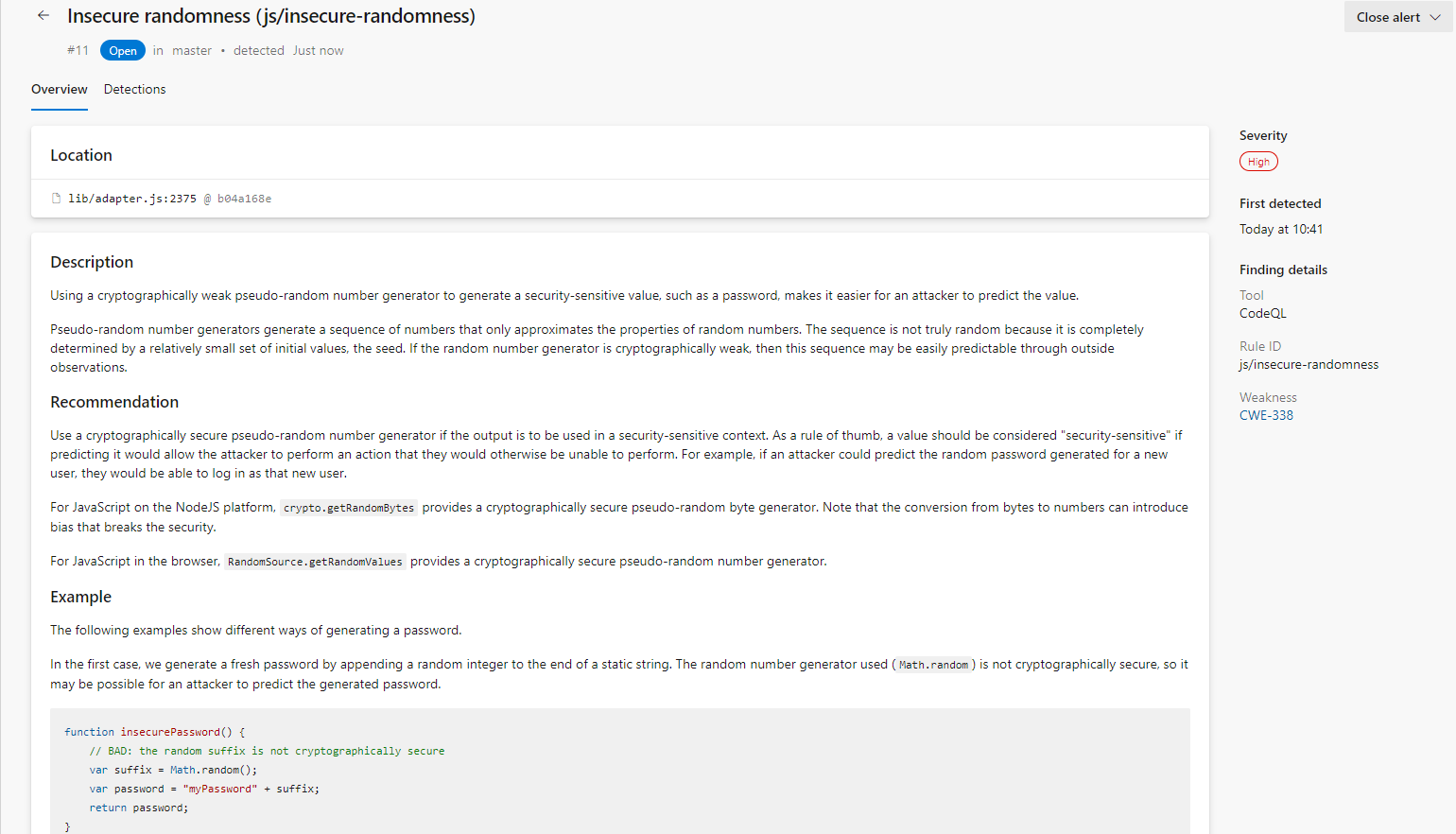
For more details about the alert, you can open each of the shown and check out detailed explanations about it, recommendations on how to fix it, examples of this type of vulnerability, and references.
The alert will automatically close if you fix the vulnerability and rerun the pipeline. If for some reason, you accept the risk or the alert is false positive, you can manually close the alert.
Secret Scanning
As described at the beginning of this article, all secrets such as keys, tokens, and similar (Mostly towards cloud providers, but not custom passwords and strings) are going to be blocked when you try to commit. In the example below, we are trying to push the App Registration Client Secret to the repository in plain text, but it is rejected since Advanced Security recognized it as a 'secret'.
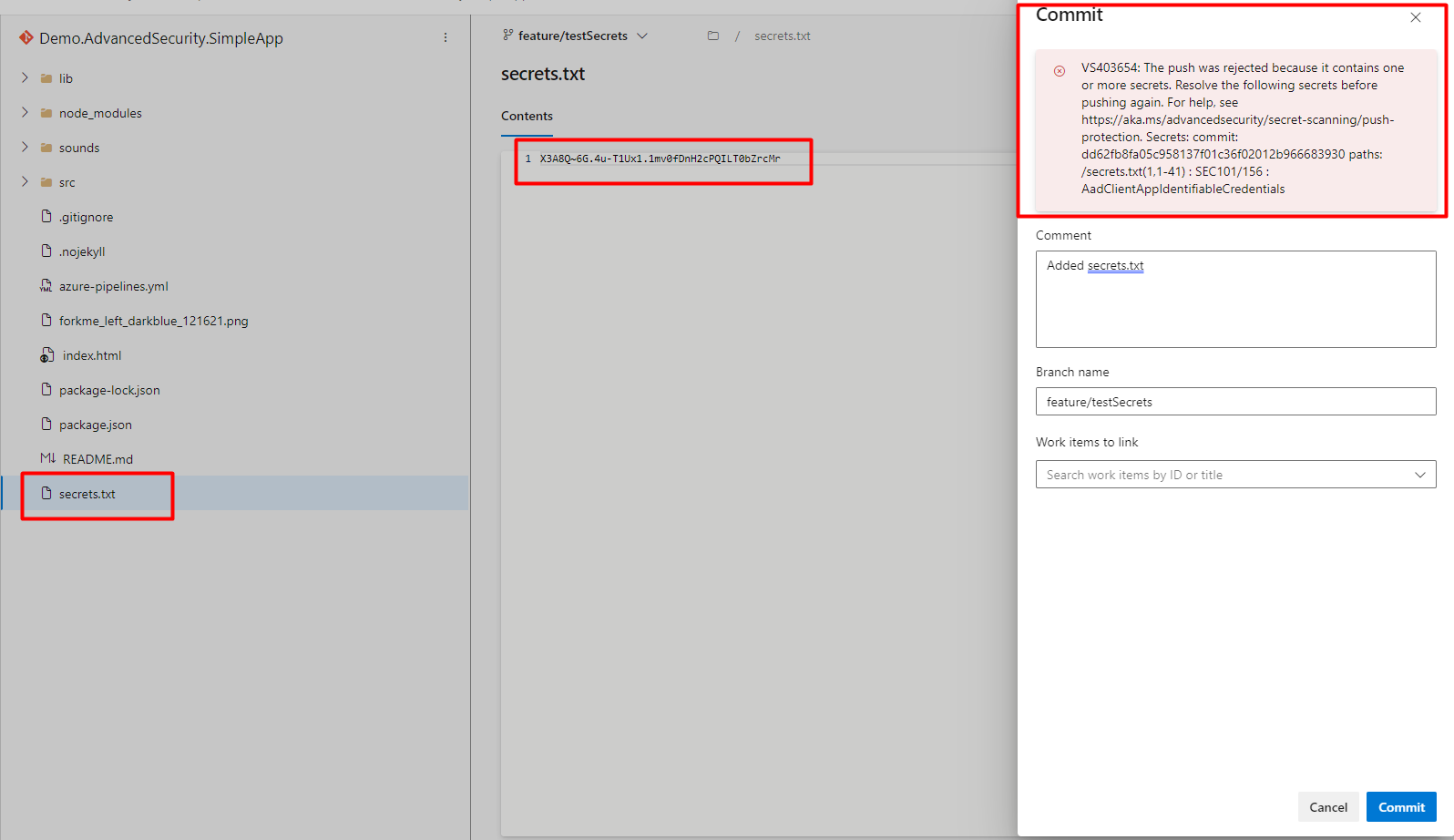
Besides this, if you just enabled Advanced Security, but have a lot of development from the past, the tool will scan all commits and files, and your exposed Secrets will be documented in the Advanced Security -> Secrets tab. After you fix the vulnerability (delete the secret, update according to secret management, and rotate the secret), the tool will still show it, so you will manually need to close it. Another approach is to use one of the tools available for git history cleanup such as BFG Repo Cleaner to clean all commit history with a specific pattern (your secret). More about it you can find here: 'https://github.com/rtyley/bfg-repo-cleaner'.
Conclusion
Advanced Security is a huge improvement for vulnerability mitigation and prevention in Azure DevOps since this type of integrated service was definitely missing. It is extremely easy to enable it in your organization, project, or repository, and document all vulnerabilities and secrets found. The next step around Advanced Security, which is already partially in place, is to connect it to Defender for DevOps.
Defender for DevOps is an Azure service that allows you visibility, posture management, and protection across different environments. In this setup, Advanced Security is more focused on the individual repository level, but Defender for DevOps would give you insight into higher levels, projects, organizations, or multiple environments. From a developer's point of view, Advanced Security is just enough to use, while Defender for DevOps would be more suitable for generating reports, general overview, and security officers governance. Defender DevOps is bringing some other functionalities besides Advanced Security, but on that topic, we will talk some other time.
Some of the features that are currently missing in Advanced Security, but many of them are already on the roadmap and coming early next year, are:
- Pull Request Build Validation – perform scans during the pull request, since today's inventory is not updated
- Break pipeline run on alert severity – break pipeline run if a high or critical vulnerability is found (or CVSS score 7 or above)
- Advanced Security dashboard – centralized Azure DevOps overview
- Custom CodeQL queries – custom queries to pass to scan
In total, great advancement in the security posture of Azure DevOps and definitely a great addition to existing features in Azure DevOps. Of course, more details about this can be found in the official Microsoft Documentation.






